Plus why OSes are like onions
If you’ve ever run into a message on your computer or other device telling you that you need higher privileges, you’ve encountered the need for “root access.”
Operating systems have to strike a balance between letting users do what they need to but without letting them mess up the entire system. For better or worse, when you have “root access” to a computer, you have the keys to the kingdom.
Operating Systems Are Like Onions
Operating systems (OSes) have layers, just like an onion. However, unlike an onion, operating systems have kernels.
The kernel is the lowest core layer of the OS. This part of the operating system talks directly to the computer’s hardware. The kernel is the first thing that loads when your computer loads the operating system. The kernel always remains in RAM. If the kernel goes wrong, the computer will crash. It’s the most critical part of the operating system.
Around the kernel are various OS components such as the file system, device drivers, Application Programming Interfaces (APIs), and User Interface (UI). The UI is the bit that connects you, the user, to all of those OS components working in the background.
Most users only need access to some of the OS components, and only to varying extents, which is why operating systems have “privilege” levels.
The Basics of OS Privileges
Just as in real life, having certain privileges in an operating system means getting access to things that users with lower privileges don’t. Access can be restricted in several ways. A common restriction is file system access. You may only have “read” privileges when it comes to specific data, which means that you can open those files and read them, but you can’t change them in any way. To do that, you’d need “write” privileges.
Some types of data may give you no “read” privileges at all. For example, you wouldn’t want a public computer to give users access to data that only staff is meant to see.
Other common restrictions relate to computer settings and software installation. Using different privilege levels, users can be prevented from installing or removing applications and changing things like the system wallpaper.
To Have Root Access is the Highest Privilege
Having “root access” means having the highest privilege possible on the computer. No files or data is hidden from you. Root users can change any aspect of the operating system.
Any application that the root user runs with the same privileges can do anything that a root user can. Root access is essential to fixing many problems and general computer maintenance.
Another term for a root user is “administrator,” although in some cases, an administrator account can have slightly lower privileges than the root account, depending on the operating system and how things are specifically configured. In most cases, admin privileges and root privileges are interchangeable terms.
Linux User Privilege Levels
Linux and other “Unix-like” operating systems have a specific approach to root accounts. There is always at least one root account in Linux, created when you first install the operating system. By default, this account is not a user account meant for daily use. Instead, whenever a regular user needs to do something that requires root access, they have to provide a username and password, which temporarily elevates privileges to accomplish the task and then drops back down to normal user privilege levels.
Using the Linus Terminal, a text-based interface, users can use the command “sudo,” which is short for “superuser do.” Any command that follows sudo executes with root privileges, and you’ll have to provide a password once again.
Windows and macOS User Privilege Levels
For years Microsoft Windows had a more laid-back attitude to root privileges. The primary user account was also the administrator account, meaning you had to manually change things if you wanted the same level of inherent safety from the Linux approach.
In modern versions of Microsoft Windows, actions that require admin privileges will trigger a Windows User Account Control (UAC) prompt, and you’ll have to provide the administrator password. You can also launch specific applications with administrator privileges. For example, you can launch the Command Prompt or Windows Terminal with admin privileges and won’t have to provide a password for the length of the session repeatedly.
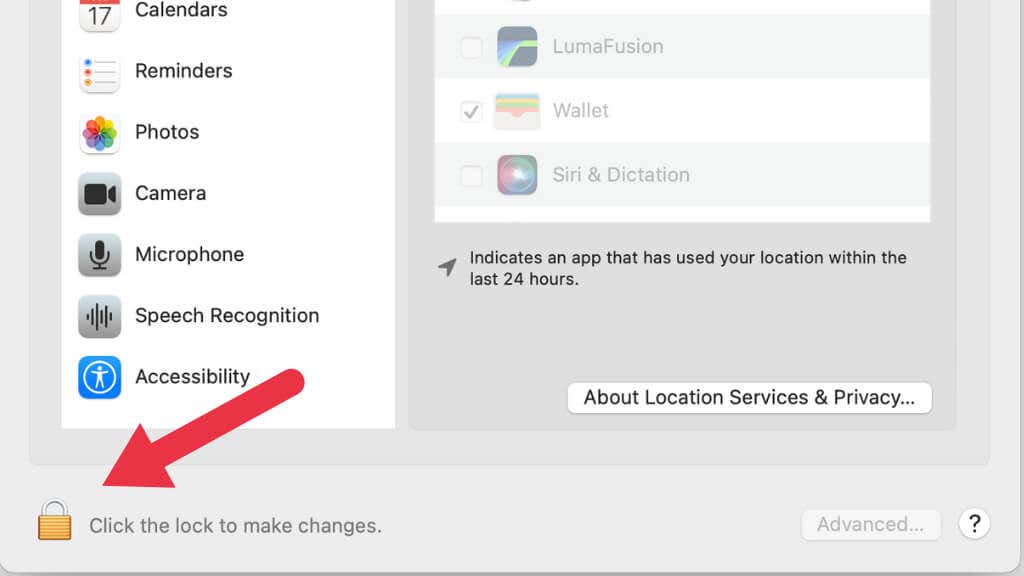
Apple’s macOS is, like Linux, a Unix-like operating system and requires a per-operation privilege elevation whenever you try to do something outside of regular use. In macOS, you’ll notice little lock icons, which let you unlock system settings with the root user password and then lock them again once you’re done.
By default, macOS is a little more aggressive with permissions than Windows. For example, if an app needs to access data on a removable drive, macOS will ask you if that’s okay the first time.
Root Access on Android Phones
Most people who aren’t system administrators first encountered the idea of “root access” or “rooting” in the context of Android smartphones and tablets. While Android is an open-source operating system, almost all Android phone manufacturers like Samsung and OnePlus don’t give their customers root access to their phones. Instead, they have special user accounts that can’t get low-level access to the phone’s hardware. So unlike a PC, you can’t change the operating system on your Android phone or make system changes that aren’t explicitly allowed by the phone manufacturer.
On many phones, root access can be gained by running a rooting app, but some devices require a somewhat involved rooting process using a computer and the Android Debug Bridge (ADB). By using one of the various one-click root methods or tutorials to root Android devices, you can get root access to your phone.
From here, you can change virtually any aspect of the device, including removing provider bloatware and disabling or enabling things the phone manufacturer wanted to keep out of your reach. Rooting an Android phone is also the first step if you want to replace the operating system completely. This can include the latest version of Android, custom ROMs, and even stock Android (like a Google Nexus phone) without the manufacturer-specific interfaces. You open up a world of alternative firmware by rooting your device and unlocking its bootloader.
Popular apps include SuperSu and Magisk, which you use at your own risk. Alternatively, spend some time on Android forums, reading about how other owners of your phone model have fared with rooting.
“Jailbreaking” iOS Devices
While Android phones don’t give you root access out of the box, Android is generally much less restrictive than iOS, even without root permissions. For example, on an Android phone, you can easily enable the installation of applications from third-party app stores and install whatever you like, even if it’s not in the Google Play Store.
On iOS, any app that Apple doesn’t approve of is simply out of reach, where the practice of “jailbreaking” comes in. The result of jailbreaking is much the same as rooting on an Android phone, but the difference is that iOS security measures must be broken using exploits.
The Dangers of Root Access
When it comes to devices like iPhones and Android smartphones, one crucial issue to consider when rooting is that it may invalidate your warranty. This is particularly worrying since a rooting or jailbreak that goes wrong can permanently brick your device, something the manufacturer may be unwilling to fix, even if you pay them.
On personal computers, the issues are different. You don’t want to give the wrong users or applications root access accidentally. Whether on a phone or computer, there’s also a chance that you may give malware root access, and that can be a catastrophe and places your system files in danger. This is why using an antivirus package is crucial on a rooted device.
Suppose you gain root access and start installing custom ROMs. In that case, you may lose access to special features of your device and see worse thermal management or battery life, as many of the optimizations aren’t present on rooted devices with custom ROMs. Some users perform overclocking on their rooted device, where the CPU and GPU are pushed beyond the manufacturer’s specifications, potentially damaging the phone.
Unrooting Your Device
What if you want to uninstall your root access? Assuming that your device still works, you can “unroot” or “un-jailbreak” it and return it to its original state, which includes flashing the OEM ROM back onto the device. You’d want to do this before selling or giving away your device, and you want to do it before trying to do a warranty return, if at all possible.
Having a rooted phone can be empowering and liberating, but it also comes with a long list of risks and caveats, so think carefully about whether it’s worth it.